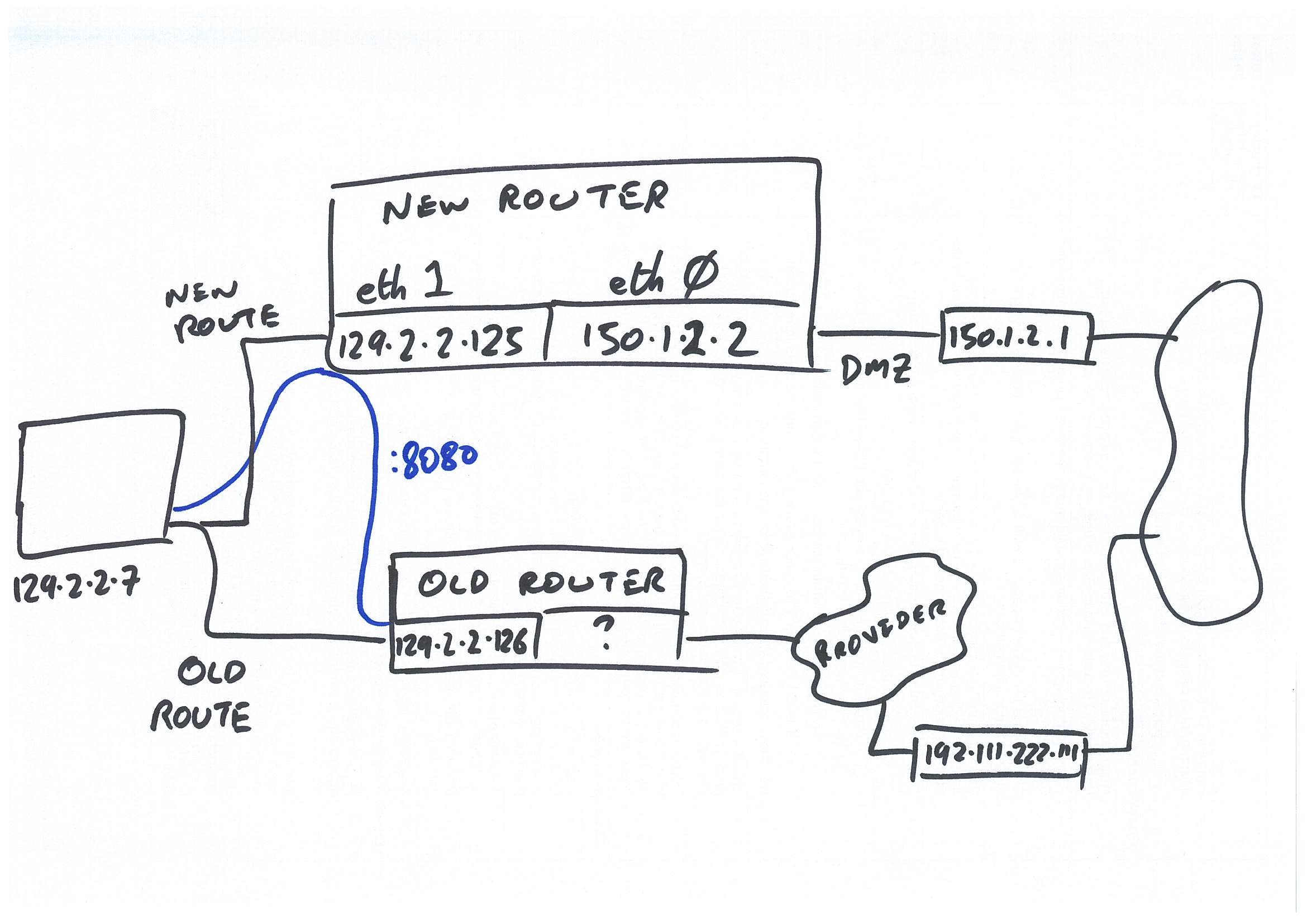
Adding persistent static routes on centos
When you need to access networks located on a different network segment, you need to have a route set up so the PC knows how to get to the other network segment. This generally just points to your main gateway, but you may want to set up additional static routes, where you don’t want the […]
Continue Reading